Kerberos Is Best Described as a Protocol for Authentication
Kerberos is used in Posix authentication. Its also an alternative authentication system to SSH POP and SMTP.
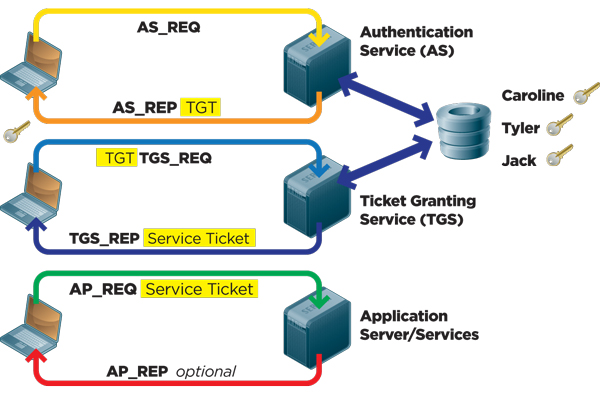
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
NTLM gives the users client no way to validate the identity of the server its authenticating to but Kerberos provides mutual authentication.

. Aside from better security Kerberos authentication also offers faster performance. Kerberos is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Kerberos uses symmetric key cryptography and requires trusted third-party authorization to verify user identities.
An authentication system developed by the Massachusetts Institute of Technology MIT and used to verify the identity of networked users. Kerberos brings a host of advantages to. Enabling a service to use Kerberos authentication is referred to as making the service Kerberos aware.
This protocol can be easily adopted even on insecure networks as it is based on a strong cryptography and its developed on a client-server model. Kerberos as a typical authentication server protocol. Authentication Protocols have discussed hash algorithms and digital signatures in abstract apart from direct use in signing messages another key use is in mutual authentication.
Kerberos is a network authentication protocol using which a node in a non-secure network can verify the identity of another node in a secure way. When a service account is set for Use any authentication protocol delegation it means that the service account is allowed to delegate without being required to prove that a user authenticated to it. Kerberos is a computer network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to.
Since Kerberos requires 3 entities to authenticate and has an excellent track record of making. Kerberos is a computer network authentication protocol which allows individuals communicating over a non-secure network to prove their identity to one another in a secure manner. Its designed to provide secure authentication over an insecure network.
Click again to see term. Kerberos version 5 is an industry standard security protocol that Windows Server 2003 uses as the default authentication service. Finally the role of Kerberos in the larger Athena picture is given along with a list of applications that.
The protocol is resistant to eavesdropping and replay attacks and requires a trusted third party. These tickets allow the nodes communicating over a non-secure network to authenticate in a secure manner. Kerberos is a computer network authentication protocol that works on the basis of tickets.
A request to access a particular service including the user ID. As per Greek mythology Cerberus or Kerberos is a multi-headed dog whose job is to guard the gates of the Underworld to prevent the dead from leaving. Understanding the Essentials of the Kerberos Security Protocol.
These are known as authentication protocols. It is used to handle authentication in Windows Server 2003 trust relationships and is the primary security protocol for authentication within domains. Kerberos is used in Posix authentication and Active Directory NFS and Samba.
In the modern world MIT Computer Scientists used the name and visual of Kerberos for their computer network authentication protocol. The Windows Server operating systems implement the Kerberos version 5 authentication protocol and extensions for public key authentication transporting authorization data and delegation. In normal words just saying I shall pass because I am the administrator trust me opens the door with no questions asked and no one.
Describes the Kerberos Policy settings and provides links to policy setting descriptions. It describes the protocols used by clients servers and Kerberos to achieve authentication. Kerberos is a widely-deployed network authentication protocol that is being considered for standardization.
This protocol was named after this mythological character. Kerberos at its simplest is an authentication protocol for clientserver applications. Knowing the basics of this pervasive protocol can be critical in troubleshooting and solving.
The views of Kerberos as seen by the user programmer and administrator are described. Kerberos uses tickets to authenticate a user and completely avoids sending passwords across the network. Kerberos is a client-server authentication protocol that enables mutual authentication both the user and the server verify each others identity over non-secure network connections.
Vulnerabilities in Kerberos authentication. It also describes the management and replication of the database required. Click card to see definition.
How the Kerberos Authentication Process Works. Many works have analyzed its security. Kerberos supports multifactor authentication MFA.
Kerberos was designed to protect your credentials from hackers by keeping passwords off of insecure networks even when verifying user identities. The basic Kerberos authentication protocol allows a client with knowledge of the users password to obtain a ticket and session key for and to prove its identity to any verifier registered with the authentication server. Kerberos is a Network Authentication Protocol evolved at MIT which uses an encryption technique called symmetric key encryption and a key distribution center.
For convincing 2 parties of each others identity and for exchanging session keys. Although Kerberos is ubiquitous in the digital world it is widely used in secure systems based on reliable testing and verification features. This is actually possible for the majority of software.
The users password must be presented each time the user performs authentication with a new verifier. The user account sends a plaintext message to the Authentication Server AS eg. Tap card to see definition.
The Kerberos version 5 authentication protocol provides the default mechanism for authentication services and the authorization data necessary for a user to access a resource and perform a task on that resource. Its designers aimed it primarily at a clientserver model and it provides mutual authenticationboth the user and the server verify each others identity. The Kerberos authentication client is implemented as a security support provider SSP and it can be accessed through the Security Support Provider Interface SSPI.
The Kerberos authentication process consists of eight steps across three different stages. The Kerberos protocol uses a symmetric key derived from the user password to securely exchange. Kerberos was designed to provide secure authentication to services over an insecure network.
The following explanation describes the Kerberos workflow. The Benefits of Kerberos Authentication.
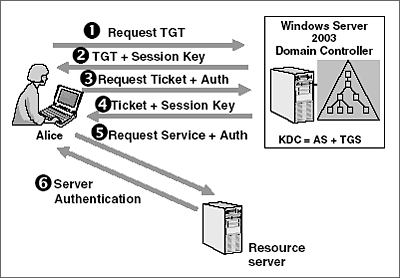
Five Steps To Using The Kerberos Protocol
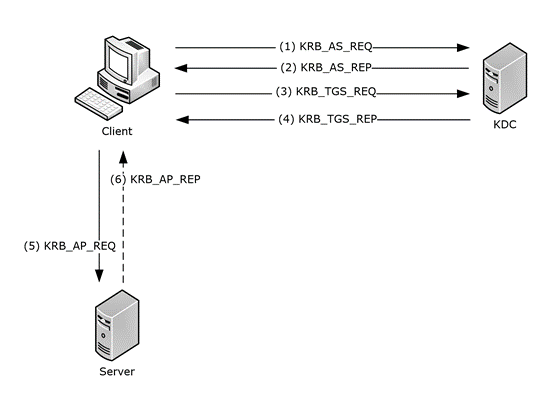
Ms Kile Kerberos Network Authentication Service V5 Synopsis Microsoft Docs

No comments for "Kerberos Is Best Described as a Protocol for Authentication"
Post a Comment